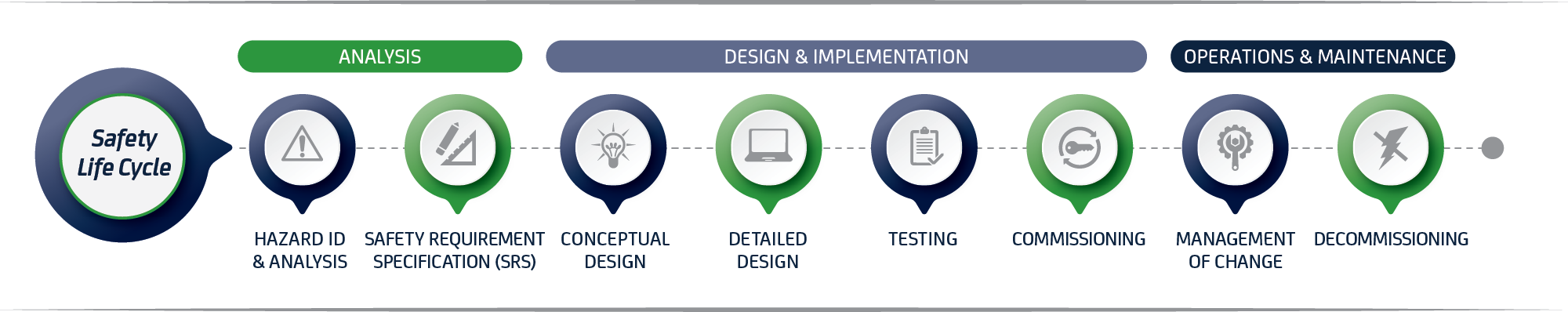
Moving data is imperative to a successful business. Whether it’s from one area of your organization to another or to an outside party, transferring information and files is part of everyday work. But if that information is particularly sensitive or proprietary, certain precautions must be made to ensure it is protected from being compromised.
Data that should be securely transferred:
- Proprietary Data – any data that must be kept private for confidential, competitive, or other business reasons. This sensitive data can be your company’s internal knowledge base, plans, communications, recipes, processes, financials, or other intellectual property.
- Client Data – any information owned by your clients that you use to do work for them. This may include batch recipes, processes, report results, etc.
Understanding the threats
The same threats to the general business IT system can also infiltrate the Operational Technology (OT) system which is the backbone of the facility. Threats to information come in many forms and usually occur from lack of diligence or knowledge on how to properly move information from place to place.
The impact? Risk of exposure. All threats to your network have the potential of stealing information that is vital to your business. This includes theft of intellectual property, identity, and information; sabotage; and even extortion of information. These threats include viruses, worms, trojans, bots, spyware, malware, ransomware, scareware, social engineering, and media attacks.
- Unintentional Disclosure of Information – malicious programs can cause your data to be shared or seen by parties for which it was not intended. Data can be skimmed, intercepted, and used as ransom.
- Compromised File Integrity – the loss or inability to maintain file integrity. Any file that can be modified proposes a security risk. Files can be intercepted and modified with malicious macros. What may look like a normal file, transferred by email or an FTP site, may now be a threat.
- At-risk Channels of Operation – the security of an entire operational technology (OT) network and control system, including all devices, is at risk. Compromised files and PCs (configuration files, OT network devices files, firewalls) can wreak havoc on the overall health and function of the control system and the operation of the facility.
Distributing proprietary information safely
With these risks in mind, what is the best way to share files? The following scenario provides a glimpse of best practices in the real world.
An operator at a chemical plant has pulled a report of emissions data. The report must be delivered to the operator’s supervisor and the state regulatory agency. This data is proprietary information to the company and required by law to be reported.
How does the file get transferred to its proper recipients, internally and outside the company?
Internal Delivery
The data from the PLC is collected by the historian into a spreadsheet file which is used to generate the emissions report. All this occurs in the Operational Technology (OT) environment, not the business IT network. The operator can safely move the report from the OT network file server to the IT network server using Windows File Sharing with security and authentication enabled.
Any time data transits security zones (e.g., OT and IT), it must be subjected to security controls, including but not limited to, authentication, threat inspection, integrity validation, information sanitation, etc.
Once the file is on the IT network server, the report can be delivered internally per the company’s established protocol. This can be by email (if permitted), by internal file server, or by an approved cloud service.
Why not just put the report on a jump drive from the OT device then load it onto the operator’s computer? Because this method yields a greater opportunity for risk. Jump drive use provides the opportunity to connect to less secure zones and unauthorized machines. This means that malware has more opportunities to be installed on this drive.
Additionally, by using Intrusion Detection Systems and Security Information and Event Management systems, it’s possible to record, correlate and alert based on activity on the network.
External Delivery
Once data leaves company-controlled servers, it enters malicious territory and becomes more vulnerable. Delivering files externally must be done in a way that ensures the information gets to its final point intact and without being exposed to the wrong parties.
Using a Managed File Transfer System will ensure end-to-end security and encryption for the data.
Managed File Transfer Advantages
- Secure from end-to-end (from sender to receiver).
- Limits admission to only those meant to have access.
- Interaction with a hosted file is logged and auditable – data is captured showing who and when the file was viewed, downloaded, changed, uploaded.
- Helps facilitate large file transfers (little to no restriction on file sizes).
- Users can request files to be sent to them from outside sources securely.
File sharing bad habits are dangerous, if not used correctly. These data transfer shortcuts are dangerous to your organization if not used properly.
Transfer Method Best Practices
- Email with attached file - Limit to non-sensitive information only. Emails can be forwarded without any control as to who sees it.
- Jump drives - Drives should be scanned for threats before each usage by a dedicated machine.
- Commercial cloud sharing sites - Never use a personal cloud site. Use ONLY those managed by your company and deemed safe.
Mitigating cyber threats
Champion has the expertise and knowledge base to help you build a secure file transfer system which aligns with industry best practices and guidelines. Here are a few ways Champion can help make your OT systems more secure.
- Perform Cybersecurity Risk Assessment.
- Install anti-virus software and keep it up to date.
- Install firewalls to create security zones and establish a DMZ between OT and IT networks.
- Deploy a SIEM (Security, Information and Event Manager) to capture instances of bad habits, jump drive use, and users to identify threats.
- Establish an Industrial Intrusion Detection System to monitor access and traffic to and from ICS and alert to abnormal activity.
- Train employees on security best practices.
Ready to learn more? Contact us today to schedule a no-cost consultation.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.
Let's collaborate.
Schedule a no-cost consultation today.

solution brief
System Hardening
More Posts