
- Home
- Author: Elise Patterson


Take a minute to imagine any or all “worst case” scenarios your facility could one day face – that if not handled properly could result in a Health & Safety event, equipment failure, or simply a loss of production. It sounds pretty ominous! But it doesn’t have to. Knowing what these situations are is the first step to mitigating risk and effectively responding – without hesitation and without panic.
Your scenarios typically don’t need to go so far as a “doomsday apocalypse” – often something as simple as a failed sensor or an unrecognized alarm could present risks with untrained personnel.
This is where Champion comes in – to create a “twin” of your control system and operating environment. In this simulated environment, we can introduce any number of scenarios, teaching first how to identify the risk and then how best to respond.
We’ve all done it from the comfort of our bed – “snoozing” that daily alarm for “just a few more minutes.” Regularly doing the same with control system alarms may be an indication you are due for an assessment by one of Champion’s Alarm Management specialists – but that is a topic for another day!
Training your personnel how to properly identify, evaluate, and respond to alarms and responding to abnormal situations in your facility is a big part of mitigating risks. Using the same example of your control system “twin,” Champion can effectively train users based on your process environment. Each possible abnormal scenario can be triggered in a no-risk environment – with users learning in each case how to respond to an abnormal situation in a timely and correct manner.
Training your workforce shouldn’t be a major undertaking – it should be a well-coordinated, preplanned, and efficient use of your personnel’s time. Champion values these goals for all clients, whether providing on-site training at your facility or at one of our strategically located facilities.
There are plenty of scenarios in which your workforce may benefit from Champion-tailored training solutions for operators, maintenance, and technical personnel. Whether getting everyone up to speed on a new system, comparing changes between a legacy and new system, or learning how to stay agile in the onsite maintenance & updates your site might require.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.
More Posts

When you have identified that it’s time to upgrade your control system, you want to explore all the options that are available to you. It is especially important to find a control system that best fits your application. For example: if you need to upgrade a controller, you will avoid upgrading the entire control system.
Some manufacturers’ control system platforms offer a variety of upgrade and migration solutions and strategies. For some end users, there are migration strategies that may be a better solution than a complete upgrade. In other cases, a complete system upgrade may be the answer. Most of the time the best solution is somewhere in between. Understanding your unique needs and expectations is vital to choosing the proper system. This can be a challenging task if you don’t have the required information.
Finding a system that meets your needs and understanding how it will function and grow with you can be a challenge. Champion's team specializes in leading clients through the process of choosing a control system that is right for their specific needs – and their budgets. As part of our process, we will work with your team to define your goals and expectations, conduct an assessment, and recommend the best, unbiased solution that aligns with your goals. We can bring your control system from the past to the present while you plan for the future.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.

More Posts

None of this would have been possible without our dedicated team, continual process improvement, and of course – our clients. We are thankful and humbled by our clients’ unwavering dedication!
Through the years, Champion has made strategic adjustments to generate a culture that inspires and empowers talented individuals to make the world a better place through technology. By always staying at the forefront of technology and investing in our team’s professional growth, our clients realize the benefits in their day to day operations.
Whether implementing a control system upgrade, designing a new installation, assessing cybersecurity gaps, improving a facility’s safety systems, or enabling secure remote access for a full suite of OT Managed Services – our commitment to excellence remains steadfast.
At Champion, we believe the success of our clients is a direct reflection of our own efforts and successes. That’s why we will continue to provide the best solutions available at any given time. Independent of any equipment manufacturer or technology platform, our experts partner with you to evaluate needs, make recommendations, and execute the rollout that brings the most value to your facility.
From all of us at Champion, we thank you for trusting in our team to provide the solutions and systems that best achieve your goals. We look forward to the next 20 years, as we continue to grow together.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.

More Posts

A security zone is created in the cloud specifically for you. Here, it serves as an extension of the Demilitarized Zone (DMZ) of your control system. The same security concepts that apply to your DMZ apply here as well.
There are only two paths in and out of your cloud zone:
These paths are restricted by routing and firewall rules to pass only the authorized data.
No windows administrative connections (RDP, WMI, RPC, and other evil acronyms) can be made from outside the DMZ and cloud zones. All administrative activity happens within the cloud zone via hosted desktop sessions. These sessions are delivered using virtual desktop presentation technologies so that only the video stream leaves, and only keyboard and mouse commands enter. No proprietary data or external threats can be transferred via either cloud path.
In order to connect your site to the cloud, a tunnel must be created. This tunnel is built using the best available VPN protocols. Like most tunnels, its job is to keep the good things in and the bad things out.
This includes:
It’s often stated that if you can’t see it, you can’t secure it. To ensure your network stays safe, it’s vital to have eyes on the traffic that’s going through it. Like a building with door sensors, motion detectors, smoke detectors, security cameras, and a remote monitoring service, Champion can be your partner in notifying you in real-time of any abnormal activity.
While opening a tunnel between your network and the cloud might sound scary, using the proper technology and partner allows your network and OT assets to be safer than ever. Not only will you be better protected from security threats, but now we can even alert you to process issues before they become big problems.
Remote support engineers can respond even quicker and without introducing you to unnecessary risks like VPN connections from untrusted computers, unmonitored persistent virtual desktop access, or cellular modems.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.

More Posts

While IT is extremely important at the corporate (or “Enterprise”) level, OT is the livelihood of any facility. The mission of any OT system is to achieve the greatest production output with the least amount of downtime possible.
Since production is the livelihood of any industrial facility, so too are the operational systems that keep them moving. Loss of production for any reason has a direct impact on a company’s bottom-line. Whether due to an outdated, unreliable platform, poor configuration, unprepared support staff, or insecure technology allowing for system breaches – many factors can affect production. Be sure to utilize an OT specialist with the experience to reach your maximum production output.
IT and OT must both be vigilant in mitigating security risks. However, IT’s risks generally lend themselves to trade secrets and corporate accountability. OT’s risks can be much more tangible: Unsafe operating conditions or monitoring can result in health and safety issues such as fatalities or environmental catastrophes.
In past years, many have taken the “air gap” approach to securing their OT control systems – keeping any production equipment separated from Internet-connected Enterprise equipment. In theory – and in a time before flash drives and smartphones – this was enough to mitigate operational risks. But, as consumer technologies emerged, so too did many large-scale security breaches affecting Industrial Control Systems.
Air gapped systems that were not physically connected to the Internet would run on outdated security patches because they were seemingly “secure.” With the advent of devices like flash drives and smartphones, however, control systems around the globe became vulnerable. Cyber-attacks could now halt production, disable critical safety systems, or result in catastrophic loss simply by altering production readings.
Having a team of Globally Certified Cybersecurity Experts at your fingertips is now vital for any industrial environment.
While the fundamental principles of IT networks are shared with OT networks, Industrial Control Systems require a much more specialized set of skills to implement and maintain. For starters, the very environment of each are vastly different. IT networks are often climate-controlled office environments, whereas OT networks can be exposed to extreme elements and process environments.
More importantly, what sets OT professionals apart is their knowledge of how to implement specific industry processes, using a range of industrial controls across multiple platforms. Lastly, they must use this knowledge to make everything communicate in an efficient, reliable, and intuitive manner.
With vast experience across numerous industries, platforms, and technologies, Champion’s OT professionals deliver on this expertise.
The natural lifecycle of IT versus OT lends itself to completely different budget approaches. While IT environments typically change every 12-18 months, OT environments can last 10-15 years or more – if they are properly designed and maintained. Therefore, planning for Total Cost of Ownership (TCO) takes not just different expertise but also a different approach and methodology to achieve a comprehensive cost.
The key to enabling Industrial Control Systems for extended durations is proper maintenance and support. In addition to cybersecurity risk mitigation, including budgetary funds for preventive maintenance and support is essential in any OT environment. As a system ages, it is key to provide regular security patches, scheduled backups, and a supply of spare parts to achieve the greatest production output.
Champion’s knowledge of these items, paired with our 24UP® Solutions, allow customers to tailor specific needs into one easily-predictable budgetary plan.
Whether for the safety of workers, surrounding communities, or environment, compliance standards are often far more stringent on OT systems. Federal and state agencies regularly monitor and regulate industrial processes due to their inherent ability to impact the community at large.
Another unique difference between IT and OT is the types of compliance each must meet. Industrial Control processes are typically subject to far more scrutiny due to their ability to impact more than a corporate entity. If improperly maintained, a process can harm employees, communities, or the environment. For this reason, it is imperative that OT systems function correctly and reliably.
OT networks continuously monitor process stages, operating temperatures and pressures, environmental emissions, leaks, or any other number of factors associated with the facility. Reliable systems improve overall safety. They also allow companies to generate real-time or historical reports for compliance agencies like the EPA, DEQ, FDA, and OSHA.
Champion engineers and professionals hold the experience necessary to implement the reliable OT systems our customers demand.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.

More Posts
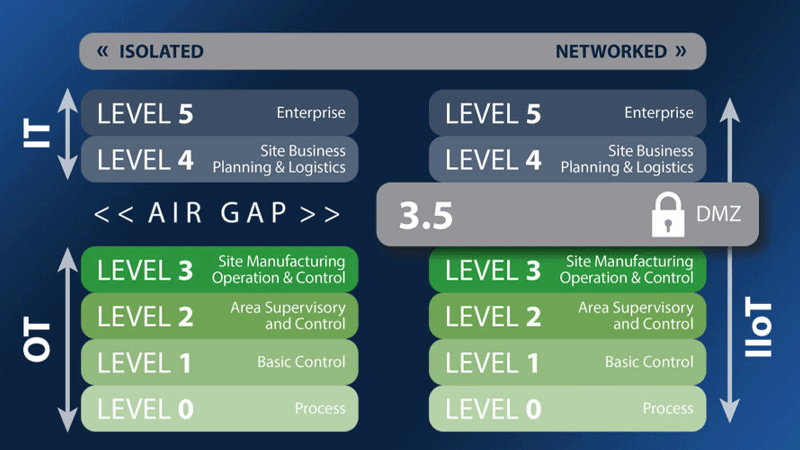
“Security by isolation” or air-gapping previously worked in Operational Technology (OT) environments when OT and IT were completely isolated from one another. Many older systems based on PLC’s and SCADA were built without cybersecurity in mind. OT and IT are now converging as organizations embrace the digital transformation, and security experts are now declaring the air gap dead as security by isolation is not a long-term solution for protecting OT assets.
Air Gapping an OT system has very limited value in today’s constant technological advances. It can no longer be used as a sole security solution in the long term for three reasons:
While air-gapped OT systems can minimize risks, organizations are not able to benefit from the highly valuable data these systems generate. Data analyzed in real time can provide business intelligence to cut costs, reduce downtime, and improve efficiency. These opportunity costs outweigh air-gapping as a viable cyber security measure.
Maintaining air-gapped OT systems are more expensive and difficult because the engineering tools of a connected system cannot be used to perform routine maintenance or troubleshoot problems. It also limits the system from secure remote support by technical experts. Without remote access, facilities experience higher support costs and increased downtime. The reality is that even a properly air-gapped system is not completely protected; Every system is a potential breach target, and even air-gapped systems can be infiltrated. Organizations must engage in active monitoring and security measures to mitigate the risks.
Air Gaps can be physically breached by a third-party networked laptop, USB drive, removable media, smartphone, or other devices. Allowing OT systems to connect with these devices creates vulnerabilities that air gapping cannot protect against. Air gapping makes it difficult for users to move back and forth between the air-gapped device and network-connected devices. For ease of use, an individual may use an unsecure USB drive to transfer data which could compromise an air-gapped system.
OT infrastructure is only as secure as the user operating the devices. An openly accessible USB port can serve as an entry route for malware. Smartphones provide another convenient route to cross air gaps when switched to Wi-Fi hotspot mode. The Wi-Fi hotspots can also be used as an entry point by hackers or those with ill intentions.
90+% of randomly found USB drives are picked up by the casual person and more than half are plugged into a PC.
Source: Kapersky
OT cyber-attacks are more dangerous in nature. An OT attack can pose risks to operational and safety systems, employees, plant, and environment. Because the outcome of an OT cyber-attack is more catastrophic, it is essential that organizations prioritize cybersecurity. While air gapping provides some security, it is not the best option to select in the competitive marketplace.
Air gapped control systems are also more vulnerable because they don’t receive the latest Windows security patches easily, therefore are usually neglected. As new virus threats emerge, the OT system will likely be unprotected, unlike its Enterprise counterpart.
We must accept the fact that air gapping as a security control is no longer a valid option. IT and OT will continue to converge leaving air gapping to be useless. Facilities should take advantage of the opportunities from integrated technologies to reduce costs and downtime while improving efficiency. While doing so, they must prioritize OT security to lessen the risk and still capitalize on the advantages of a connected IT and OT world.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.

More Posts

24UP® Solutions is Champion’s premier Industrial Control System, Operational Technology, and Industrial Cybersecurity solution led by the experts who have seen it all. Clients rely on 24UP® to ensure a proactive response to issues that often arise, but are often not considered – or simply haven’t had the time to address.
Whether simply providing you with the tools to be prepared for unexpected challenges, or being your primary provider of maintenance and 24/7 emergency support – we work with you to tailor a plan that fits your needs and budget. Your company’s 24UP® Solutions could include your highest need to help you achieve your goals, including:
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.

More Posts

Champion, with expertise in every major industrial control system, supports all parts of your facility’s systems under one agreement tailored to your specific needs. Typically, response times are quicker than a manufacturer would be thanks to the scope and experience of our team. Combined with our Secure Remote Support offerings technology, we are able to provide you services anywhere at any time.
Whether your facility already has in-house support staff, or requires a primary support contact, Champion can offer guaranteed response times based on your needs. Industrial clients can also benefit from our multi-vendor support by receiving unbiased recommendations about system upgrades, network configuration, cybersecurity, and more.
Lastly, Champion’s 24UP® Solutions often save clients money over multiple OEM service contracts or in-house support staff with a ‘one stop shop’ support solution for your industrial control systems and Operational Technology (OT) assets. So whether you prefer a secondary support option or a full umbrella of support, we can tailor and provide the right solution for your needs and budget.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.

More Posts

One of the first investments your organization can make is to perform a Cyber Criticality Assessment. A Cyber Criticality Assessment is a process that allows organizations to identify general threats, determine the worst-case impact, whether it’s Financial, Safety, Health, Environmental, or otherwise, of devices/software becoming unavailable, unreliable, or compromised. The assessment process includes a survey, a vulnerability assessment, and a risk assessment to allow your organization to determine the severity of the consequences should a device or network not perform as intended.
There are key benefits to inviting a professionally certified, expert third-party team to perform your cybersecurity assessment.
Third-Party Assessment teams do not represent any hardware or software manufactures. This enables them to take an unbiased approach to your system. While internal teams may have critical knowledge of your control system and may have even designed it, third-party assessors can see both macro and micro-levels of your control system. They will see gaps in a system that internal teams can miss.
This is doubly important when it comes to Operational Technology (OT) and Industrial Control Systems (ICS) because all control system manufacturers have their own products and solutions for implementation. An unbiased third-party assessment team, especially one with a deep understanding of OT systems can connect manufacturer solutions with industry best-practices for solutions that fit your requirements.
The cybersecurity industry is expanding and growing at an astounding rate, and the demand for qualified and experienced professionals is fierce. Even when they can’t find qualified professionals to hire, many companies are still hesitant to hire outside help. According to a Kaspersky study released in 2018, 92% of companies who participated in the Kaspersky study prefer to maintain in-house OT and ICS cybersecurity personnel [1]. At the same time, 58% percent of companies find it difficult to find and hire employees with the necessary skills to address their organization’s OT/ICS cybersecurity challenges [1].
If not, consider working with a third-party OT/ICS cybersecurity team who has the expertise and personnel to do the bulk of the work for you.
Cooperation and collaboration between OT and Information Technology (IT) is critical for your company’s complete, comprehensive cybersecurity investment. But does your IT team have OT knowledge and expertise?
A third-party assessment team with an OT/ICS background can connect manufacturer products and solutions with industry best-practices and methodologies that meet your requirements. They fill in the OT knowledge gaps that your IT team may lack. For example, assessors with OT backgrounds can provide insight on which control hardware your system uses that meet ISASecure® standards [2]. This is especially critical if your control system uses hardware and software from many different manufacturers.
A top-rated cybersecurity team with both IT and OT backgrounds can help to ensure that your cybersecurity assessment includes all aspects of your control system and business networks while working with your already-established IT team.
If you’re interested in learning more about Cybersecurity System Assessments for your system and establishing a strong foundation for your company’s cybersecurity policies and procedures, click here to reach out to Champion’s team of cybersecurity experts.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.
[1] Kaspersky, “2018-Kaspersky-ICS-Whitepaper.pdf,” 2019. [Online]. Available: https://ics.kaspersky.com/media/2018-Kaspersky-ICS-Whitepaper.pdf
[2] ISA, [Online]. Available: https://www.isasecure.org/en-US/Certification
Savoy Stewart, “firms-investment-on-cyber-security-by-industry,” [Online]. Available: https://www.savoystewart.co.uk/blog/firms-investment-on-cyber-security-by-industry

More Posts
Page [tcb_pagination_current_page] of [tcb_pagination_total_pages]