
- Home
- Author: Elise Patterson


A well-planned DR plan can mitigate the impact of disruptions, protect critical assets, and ensure business continuity in the wake of a catastrophic event. However, simply having a plan on paper is not enough. To ensure your DR plan’s effectiveness, it must be tested, regularly maintained, and integrated into your organization's overall risk management strategy.
Regular reviews ensure the DR plan is comprehensive, accurate, and in alignment with the organization’s operations and technology. Further, it can illuminate potential gaps or areas for improvement. Methods include:
Verification is the process of testing the backup and recovery systems to ensure functionality is as intended. Elements include:
Ensure that all relevant personnel, from front-line OT operators to IT staff, are thoroughly trained on their roles and responsibilities in the event of a disaster. This includes understanding the DR plan, knowing how to activate it, and being familiar with the procedures for recovering critical systems and functions.
A robust Disaster Recovery strategy is not a luxury but a necessity. Remember: it’s not if, but when.
From maintaining safe operations to safeguarding your organization’s reputation to mitigating overall impact, the testing and verification of DR plans is essential to ensure your organization is prepared for challenges that will arise.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.

More Posts

Digitalization is the integration of digital technologies to automate processes, optimize workflows, and achieve operational excellence. Gartner describes digitalization as “the process of moving to a digital business.”
This means connecting machines, systems, and people through a digital network to collect, analyze, and utilize data for improved decision-making. Successful digitalization facilitates innovation and creates sustainable value.
With the increasing connectivity of OT systems, cybersecurity measures have become critical to protect against cyber threats.
Impact: Advanced cybersecurity solutions, such as anomaly detection and threat intelligence, help secure OT environments from attacks like ransomware and other forms of cyber intrusion.
Integration of sensors, devices, and machinery with internet connectivity, enabling the collection and analysis of real-time data.
Impact: IIoT enhances operational efficiency, predictive maintenance, and real-time monitoring, allowing companies to optimize processes and reduce downtime.
Edge computing processes data closer to the source (i.e., at the edge of the network) rather than relying on centralized cloud computing.
Impact: Reduces latency and enables real-time decision-making for more reliable and secure data processing in OT environments.
AI and ML technologies analyze vast amounts of data to identify patterns, make predictions, and automate decision-making processes.
Impact: AI/ML drives advancements in predictive maintenance, quality control, and process automation, leading to more efficient and reliable operations.
Data analytics tools process and analyze large volumes of operational data to provide insights and support decision-making.
Impact: These tools improve operational efficiency, reduce waste, and help in the identification of trends and potential issues before they become critical.
The future of digitalization holds boundless potential for innovation and growth in OT environments driven by the convergence of IT and OT. Enhanced data analytics and the integration of cyber-physical systems, along with a focus on sustainability, will lead to more autonomous, efficient, and secure operations, further enhancing the resilience and adaptability of OT environments.
By harnessing the power of emerging digital technologies, businesses can achieve significant improvements in efficiency, productivity, and competitiveness with those embracing digitalization leading the way.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.

More Posts


Vulnerability management assessment (VMA) and penetration testing (pen testing) are critical to a proactive cybersecurity strategy. The traditional reliance on manual scans and analysis meant these processes were slow and tedious. AI and ML are changing that.
With the ability to quickly analyze vast amounts of data, AI and ML enable accurate threat prediction, prioritization, and mitigation. These models can continuously learn and adapt to new threat intelligence and dynamically respond to the rapidly evolving threat landscape.
Today’s cybersecurity measures must account for the rise in interconnected systems and devices and the new opportunities to exploit human fallibility inside this environment. Focusing on external threats alone isn’t an option.
User Entity and Behavior Analytics (UEBA) leverages AI and ML to identify a broader range of threats– such as inside actors, social engineering, and brute-force attacks. By continuously analyzing user behavior patterns, anomalous activity detection is honed and accelerated– allowing for more informed preventative action and enforcement of regulatory compliance.
Teams are often bombarded with cybersecurity alerts– many of which can be false positives– leading to alert fatigue, wasted resources, and delays in addressing critical threats. These delays can trigger cascading security breaches. AI and ML can streamline this process by filtering out false positives, automating threat responses, and highlighting the most critical threats.
Automated responses can address low-risk alerts, block malicious access attempts, and quarantine compromised devices or networks. These measures can minimize the damage of cyberattacks and enable human experts to focus on higher level initiatives and high-priority incidents.
The future of cybersecurity is inextricably intertwined with AI and ML. As these technologies continue to evolve, so too will their ability to detect, prevent, and respond to cyber threats. Empowered by AI and ML, security teams can proactively safeguard systems today and prepare for the ever-evolving threat landscape of tomorrow.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.

More Posts


By working collaboratively with your team to understand your processes and needs, we will develop a phased approach that integrates seamlessly and minimizes disruption. Ongoing support from our team will bring continuity from implementation to maintenance, ensuring smooth operation.
We understand the challenges of securing legacy systems. Our team employs a layered security approach– including network segmentation and access control– to strategically mitigate risk.
The global cybersecurity talent gap makes building and keeping a top-tier in-house team a constant uphill battle. Partnering with a dedicated solution provider like Champion offers a scalable solution. From meeting compliance standards to implementing cutting-edge tech and innovative strategies, our expert team has you covered.
The cost of a successful cyber attack can be astronomical– encompassing operational disruption, financial loss, and enduring reputational damage.
Recovering a single GB of data from a ransomware attack cost an average of $53,000 in 2023.*
Our risk-based approach and tailored solutions provide measurable improvement in your security posture and maximize your ROI.
Industrial organizations can no longer afford to overlook cybersecurity. With the ever-evolving threat landscape, a robust security posture is essential for protecting critical infrastructure, ensuring operational continuity, and safeguarding valuable data. Our team is here to keep your operations running safely and securely so you can focus on what you do best.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.
*The Global OT & IoT Threat Landscape Assessment and Analysis Report, Sectrio, 2024

More Posts
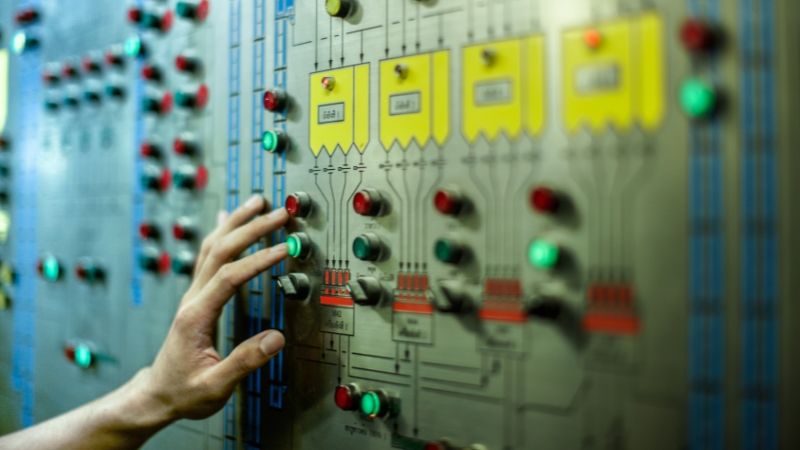
Legacy systems may include components that are decades old– meaning their designs never accounted for modern cyberthreats and the implications of digital convergence.
As these systems reach end-of-life (EOL), lack of updates and patches, discontinuation of vendor support, and incompatibilities with emerging tech compound the risk of critical disruption.
By isolating critical systems, you can reduce the spread of cyberattacks and limit the potential impact of security breaches.
Regular reviews of cybersecurity policies and controls can identify vulnerabilities, ensure regulatory compliance, and uncover inefficiencies.
Enforcing strong authentication, authorization, and accountability mechanisms ensure only the necessary personnel have access to critical systems.
Developing and routinely testing an incident response plan enables the efficient identification and mitigation of cyber incidents.
Integrating new tech into legacy OT systems can seem daunting, but with an informed understanding of the risks and a commitment to implementing best practices, you can protect your organization’s critical systems and stay competitive in the digital age of industry.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.

More Posts


Page [tcb_pagination_current_page] of [tcb_pagination_total_pages]