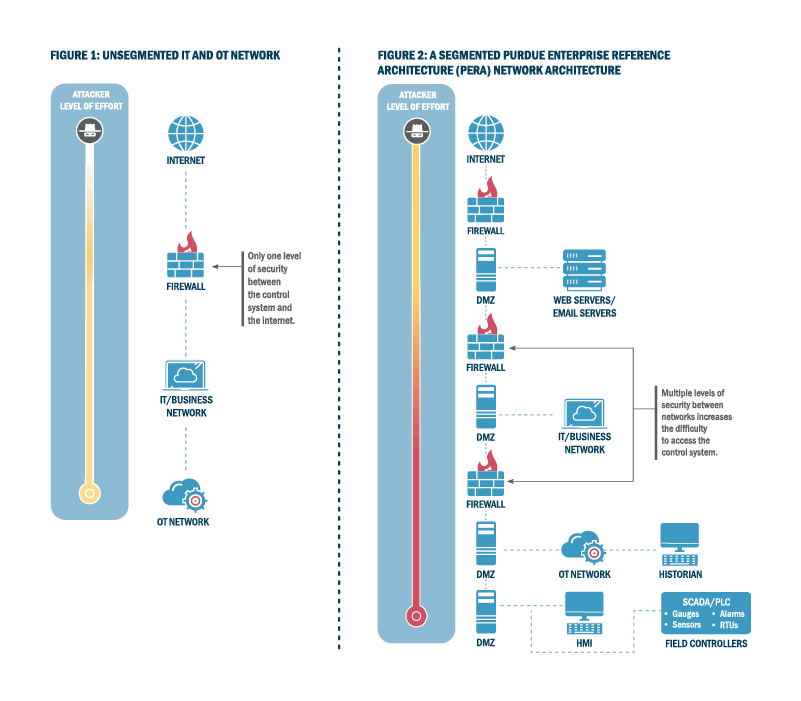
🛡️Why Network Segmentation Matters
Network segmentation is a cornerstone of OT cybersecurity. It involves dividing a network into isolated, secure zones—either physically or virtually—each acting as a self-contained subnetwork. This approach:
- Reduces risk
- Enhances control
- Prevents lateral movement in the event of a breach
The Cybersecurity and Infrastructure Security Agency (CISA) emphasizes the importance of segmentation and provides a clear, actionable framework for its implementation—especially for critical infrastructure environments.
Top 5 Benefits of Network Segmentation
- Threat Containment: Compromised systems are confined within their segment, preventing wider disruption.
- Smaller Attack Surface: Limiting inter-zone communication reduces paths for attackers to reach sensitive assets.
- Protection of Critical Assets: High-value systems like DCSs, PLCs, HMIs, and control servers are isolated from less secure IT zones.
- Improved Monitoring: Smaller zones allow for more precise anomaly detection and event tracking.
- Compliance Enablement: Helps meet requirements in frameworks like ISA/IEC 62443, which mandate segmentation as a baseline control.
Key Components of an Effective Segmentation Strategy
1. Define and Group Zones
Organize assets by function and risk level. Typical OT zones include:
- Control Zone: PLCs, DCS, SCADA, most critical layer.
- Historian Zone: Operational data aggregation.
- MES Zone: Operational-to-enterprise handoff.
- Remote Access Zone: For secure third-party or vendor access.
- Enterprise IT Zone: Business apps and office systems.
2. Establish Secure Conduits Between Zones
- Strict Communication Rules: Permit only essential traffic between zones, with defined protocols and endpoints.
- Firewalls with ACLs: Use industrial firewalls and Access Control Lists to strictly manage inter-zone traffic.
- DMZ Deployment: A DMZ acts as a secure proxy zone between IT and OT, preventing direct access while enabling controlled data exchange.
What is a Demilitarized Zone (DMZ)?
A secure buffer that separates critical OT systems from external or enterprise networks.
3. Test, Monitor, and Maintain Continuously
- Validate Controls: Post-deployment testing ensures segmentation functions correctly without disrupting operations.
- Continuous Monitoring: Track traffic flows and flag deviations or unauthorized access attempts.
- Ongoing Review: Update policies as new assets or threats arise.
🏆 The Champion Advantage
Effective segmentation requires more than IT knowledge, it demands a deep understanding of industrial processes. That’s where Champion Technology Services excels.
We deliver segmentation strategies that:
- Protect operations without disrupting uptime
- Align with CISA guidance and industry specific standards
- Bridge IT security best practices with OT realities
We combine cybersecurity leadership with control system expertise to design and implement resilient, scalable, and compliant network architectures for critical infrastructure environments.
Ready to learn more? Contact us today to schedule a no-cost consultation.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.
CISA Recommendations
- Segment high-value assets into isolated, high-security zones.
- Use firewalls with specific access control rules.
- Create a DMZ for critical cross-domain operations.
- Limit access to DMZ devices through defined user and device lists.
- Restrict data traffic from OT to IT, particularly for remote access.
Let's collaborate.
Schedule a no-cost consultation today.

solution brief
Network Segmentation
More Posts