OT Cybersecurity Gap Assessments: The First Step Toward a Safer, More Reliable Operation
For industrial organizations, building a mature cybersecurity posture starts with clarity. You can’t improve what you can’t see, especially in complex OT environments where aging systems, undocumented devices, and day-to-day operational pressures create blind spots.
A gap assessment gives OT teams that clarity. By comparing your current controls, policies, and procedures against frameworks like NIST CSF, ISA/IEC 62443, or NERC CIP, it delivers a clear, prioritized roadmap tailored to your operations. For operators, technicians, and engineers, the impact is direct: improved uptime, reliability, safety, and long-term system health.
What an OT Gap Assessment Is and Why It Matters
A gap assessment evaluates your OT environment against a defined target state built on industry standards, regulatory requirements, and operational needs. It enables you to understand:
- Your true security posture
- Operational weaknesses tied to legacy systems or manual processes
- Misalignments between policy and reality
- The highest-impact improvements to reduce risk
OT systems can’t simply be rebooted or patched whenever convenient. Every change must protect safety, reliability, and process continuity and a gap assessment ensures your controls and processes support those realities.
For OT personnel, the benefits include:
- Better visibility into aging and undocumented assets
- Reduced troubleshooting time
- Increased confidence in system reliability
- Early insight into modernization and lifecycle requirements
- Stronger justification for budget and resource planning
A gap assessment shifts the conversation from “Is our firewall configured correctly?” to “Do our systems and processes support long-term operational health and safety?”
What to Expect During the Assessment
The process is collaborative and designed to minimize operational disruption. It focuses on how your facility actually works, not just what’s documented.
Typical activities include:
- Documentation Review: Architecture diagrams, control system configurations, network designs, and backup procedures
- Field Validation: Walkdowns in control rooms, server cabinets, and field panels to verify what actually exists
- Workflow & Access Review: Operator practices, account usage, change management, and legacy “tribal knowledge”
The goal is a clear, accurate understanding of your current environment.
Key Components of an OT Gap Assessment
1. Baseline Evaluation
We document how systems are designed and operated today, capturing real-world conditions such as unsupported operating systems, end-of-life controllers, unmanaged network devices, vendor-installed assets, and manual processes that introduce operational risk.
2. Target State Definition
Together, we establish a realistic target state aligned with NIST CSF, ISA/IEC 62443, regulatory obligations, and your operational priorities.
3. Gap Identification
We highlight where your environment diverges from best practices across segmentation, access control, backups, patching, monitoring, governance, and system lifecycle practices and explain what each gap means for uptime, safety, and reliability.
4. Remediation Planning
We build a prioritized roadmap that accounts for downtime windows, staffing, investment needs, and alignment with ongoing modernization efforts. Every recommendation is practical for a 24/7 industrial environment.
What We Typically Find and Why It Matters
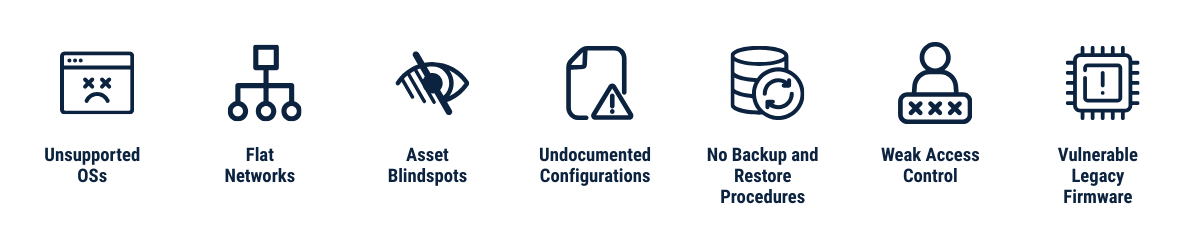
Across assessments, common issues include:
- Unsupported or unpatched operating systems
- Flat networks with limited segmentation
- Outdated or incomplete asset inventories
- Poorly documented configurations
- Lack of formal backup/restore procedures
- Shared accounts or unmanaged access
- Legacy firmware with known vulnerabilities
These conditions are typical in long-lived OT systems. A gap assessment simply makes them visible so improvements can be planned objectively and cost-effectively.
Key Takeaway
A gap assessment is the foundational step toward building a resilient OT cybersecurity and operational program. It provides clarity, actionable priorities, and a realistic roadmap grounded in your operational reality.
For OT end users, it delivers what matters most: safer operations, fewer disruptions, and a more reliable control system environment.
🏆The Champion Advantage
We don't just assess, we also implement remediations. Many firms can identify gaps, Champion closes them.
Deep OT Expertise
Our engineers understand legacy and modern control systems across PLC, DCS, SCADA, networking, virtualization, and system architecture.
From Findings to Implementation
We don’t stop at recommendations. Our teams execute the remediation work, whether that means:
- Segmenting networks
- Deploying firewalls or access control improvements
- Updating or migrating control systems
- Virtualizing servers
- Implementing backup/DR solutions
- Replacing outdated PLCs or infrastructure
- Supporting DCS modernization or on-process migrations
You get a partner who can take your roadmap from paper to production.
Proven in Live Industrial Environments
Our methodology has been refined across various critical infrastructure industries, without jeopardizing operational continuity.
Integrated Support
We work closely with operators, engineers, and IT/OT teams to ensure every improvement aligns with real workflows, staffing, and maintenance constraints.
Your assessment becomes a fully supported execution plan, not homework.
Ready to learn more? Contact us today to schedule a no-cost consultation.
We empower our clients to build safe, sustainable operations by delivering comprehensive Operational Technology (OT) solutions. From concept to implementation and beyond– we'll be there every step of the way.
How Gap Assessments Support Modernization
Many organizations begin with a gap assessment before embarking on broader modernization efforts like:
- DCS upgrades
- Virtualization
- On-process migrations
- Network redesigns
- OT data center development
By identifying aging assets, unsupported software, and high-risk configurations early, the assessment ensures modernization plans are cleaner, safer, and more cost-effective.
Let's collaborate.
Schedule a no-cost consultation today.

Article
A Guide to Cybersecurity Assessments
More Posts